
A complete ransomware strategy includes reducing the risk of a successful attack and reducing the effect of a successful attack. There are five basic rules you need to follow in general: plan, prevent, monitor, restore (quickly), and test.
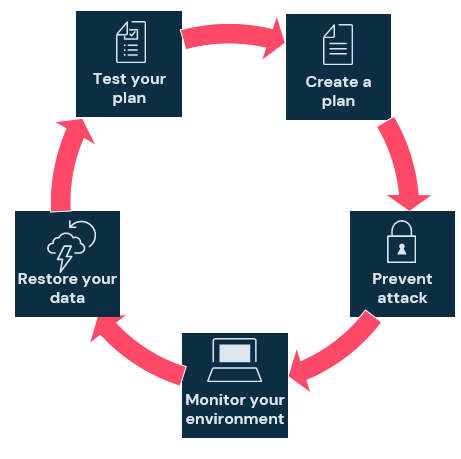
1. Create a Plan: An effective plan is the basis of resuming normal operations completely and quickly.
2. Take Precautions Against Attacks: Proactive steps including OS compression, application compression, and ransomware protection.
3. Monitor Your Environment: Always keep an eye out for anomalies by detecting an attack as quickly as possible to mitigate its effect.
4. Perform Restore Tests: Normal Restore quickly with an intact data copy to resume the business operations quickly and mitigate the effect of ransomware.
5. Test Your Plan: Perform frequent tests to verify that you can meet the SLAs you’ve defined for high-priority data and applications.
1- Create a Plan: An effective plan is the basis of resuming normal operations completely and quickly.
Defines and prioritizes critical applications. While defining Recovery Point Objectives (RPO), Recovery Time Objectives (RTO), and Service Level Agreements (SLAs) of your systems, data, and applications.
Which players (internal and external) will be involved in your data recovery efforts? Contact? Escalations?
Location and media information for 3-2-1 backup strategy?
2- Take Precautions Against Attacks: Hardening is the process of removing the processes including services, protocols, configurations, background procedures, etc. that are not required for system functionality. Essential hardening focuses on the basic operating systems, applications, and webservers that Commvault platform needs for proper operation. Security vulnerabilities in basic technologies can be the essential cracks used to jeopardize the integrity of Commvault data protection platform and risk the protected backups. Commvault needs to adapt itself as the organizations develop and apply hardening infosec policies.
3. Monitor Your Environment: No matter how consistent and effective your countermeasures are, you have to assume that at some point, ransomware will enter your environment. At that point, the focus shifts to monitoring: detecting the attack as quickly as possible so you can reduce its impact. Detection can include scanning servers for anomalies such as unusual file system behavior that can signal that an attack is underway. Machine learning has become a key asset in this effort, using historical data to recognize the difference between legitimate activity and potential trouble signs. Honeypots take detection one step further by creating a hidden file of a type that’s especially appealing to hackers and monitoring it for signature changes and other anomalies.
What Commvault DOES NOT DO:
Scan and remove malware / ransomware
Prevents ransomware from spreading to backup data from external sources.
Change the security software and best security applications
4. Perform Restore Tests: Fast restores can greatly reduce the impact of a ransomware attack. Not only do you still have an intact copy of your data — you also can make it available to systems and users quickly so you can resume normal business operations.
There are three ways to back up data, each with different implications for restoration.
Traditional backup operates at the file level. The system works through all the files and directories in the volume to determine whether they’ve changed and need to be part of the current backup. This can be a time-consuming and resource-intensive approach, though, as the system has to navigate every part of the index — an aptly named “tree walk.”
Block-level backup avoids the performance penalties of traditional backup by working on a block-by-block basis. The application doesn’t care how many files there are or what your index looks like. That allows faster, more efficient backups, which in turn makes it feasible to perform backups more frequently.
Replication takes a continuous approach to data backup. One way to do this is through continuous data replication (CDR), which involves logging all file write activity on the source computer, transferring this log to the data recovery platform, and replaying it to create a near real-time replica. Another option is to use incremental replication to continuously apply changes from a source backup to a synced copy of the backup. Volume block-level replication (VBR) is often the best approach, combining the efficiencies of block-level backup with the near real-time advantages of replication. This allows granular point-in-time recovery, crash-consistent recovery points, application-consistent recovery points and effective recovery point lifecycle management.
5. Test Your Plan: Once you have your plan in place, along with the procedures and technologies to execute it, make sure it’s going to work as needed. Perform frequent tests to verify that you can meet the SLAs you’ve defined for critical and high-priority data and applications.
Recovery Orchestration - Commvault main server can be fully recovered with a single click, which can be tested ahead of time by a fully orchestrated test failover to provide a validated restore without disrupting production.
Data Integrity Validation - Commvault provides multiple methods of data integrity validation. CRC check on the network before and after data acquisition during backup and validation of the data read from the backup environment media during restore. In addition, automated tasks for regularly validating the data on storage are provided.
Backup Validation – Fully orchestrated application recovery validation job can link a data protection virtual machine copy from a backup infrastructure, launch the application, connect and run a test method and create reports.
Commvault enables the clients to recover their business operations at any time within their desired recovery time objectives by protecting the data, applications, and workloads.
| Potential Threat Actors: | Threats: |
|---|---|
| Insider non-malicious | Sensitive data leaks |
| Insider malicious | Business and reputation |
| External - hackers, exploits | Loss of production data |
| Loss of backup data |
Cyber threats risk the recovery readiness…
Trust Commvault to protect your data, applications, and workloads and thus ensure that the data is recoverable and business operations are restorable in case of a disaster.
The purpose of Commvault’s security and ransomware software is to protect the backup data against virus infections, removal, modification or corruption. Thus, protected the backup data by ensuring backup platform security.
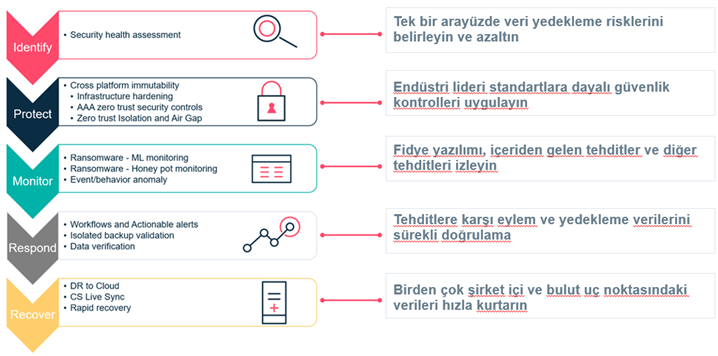
Commvault’s aforementioned 5-step secure backup and restore framework consists of feature groups, standards, and instructions to manage the cybersecurity risks of backup data and ensure that the data are ready for restore.

Commvault gives you rigorous control over data access.
Accordingly, know your data, Identify and Assess the Risks
Commvault provides a unique data protection set for the workloads of end users offering broadest range of platform support compared to its competitors. You can back up your data with Commvault regardless of location and protect against attacks.

Commvault has many more abilities for your data in addition to backup operations. However, we’ll not go into detail since that’s not our point. I recommend viewing our File Storage Optimization, Data Governance, eDiscovery&Compliance products if you’re interested. You can view your data with a single interface using these products and take extra security precautions based on the location of the data.
 Verification and Access Permission |
Commvault Authentication

|
 Access Levels Control |
Commvault Authorization
|
 Access and ability monitoring and auditing |
Commvault Monitoring & Audit
|
Authentication controls provide and grant access to backup data. This can be thought of as the “gate-keeper.” Features include certificate authentication, two-factor authentication (2FA) and integration with multiple third-party identity providers using secure protocols such as LDAPS, SAML and OpenID.
Authorization controls determine what level of access is allowed on the CommCell. Once authentication is allowed, it has various controls such as role-based security, multi-tenancy, privacy locks and multi-level authentication. Each of these features work in tandem to protect data from being accessed, retrieved and deleted. Adding these gates create software isolation, where even administrators are blocked from deleting and accessing backup data as well as reversing security controls. Similarly, if a malicious actor steals access into the CommCell, the backup data is secured from malicious activity within the backup data platform.
Lastly, it enforces Accountability by auditing events, and actions within the CommCell and providing a rich customizable interface to view this information. Hundreds of reports are readily available in the store providing deep information on the operations, events and action of the CommCell. Information within reports and dashboards is only visible to users given access. This allows owners to view the same audit reports and dashboards as Administrators, without seeing resources they do not have permission to see. The ability to customize and create your own reports using data sources, and external APIs, is useful for expanding its capabilities and power. For continuous monitoring, integrates with third-party tools such as Syslog, Splunk and SNMP systems. This further expands the accounting and audit capabilities within Commvault and provides flexibility to integrate with whatever systems are already.
You can maximize your security level using the interface to increase the security of protected data thanks to Commvault’s custom dashboard. You just need to follow the instructions on the dashboard.
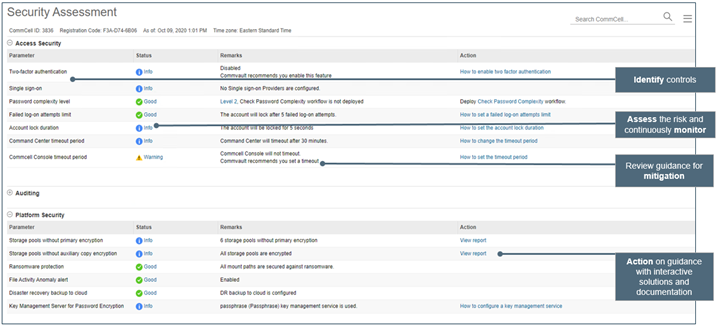
Security Health Assessment Dashboard provides a single view for IT Administrators to rapidly harden the security posture, identify risks in real-time, take corrective actions, and rapidly recover the data.
Continuously improves the security posture allowing you to stay ahead of ransomware and emerging threats.

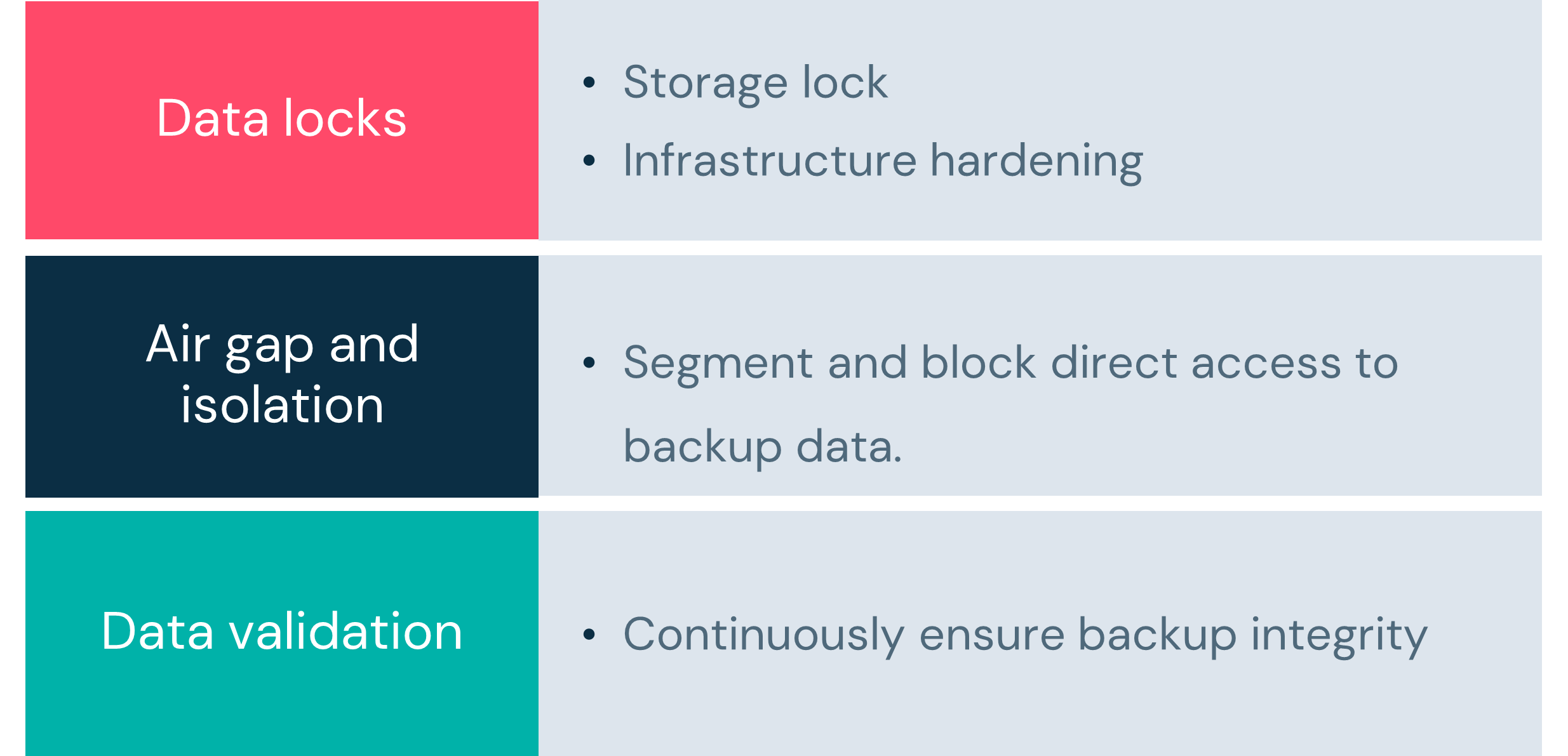
- Storage Lock (Storage I/O Controls)
Commvault locks storage by monitoring I/O requests and only allowing access to authenticated and authorized Commvault binaries. Developed for RedHat/CentOS/Windows operating systems and Commvault HyperScale and HyperScale-X SDS structures.
- Infrastructure Hardening


Harden infrastructure using CIS and STIGs to reduce the attack surface.
CIS and STIG are two primary third-party baselines adopted across public and private organizations for infrastructure hardening. Both hardening standards share many similarities; however, while CIS is primarily adopted across a wide range of commercial organizations, STIGs are primarily used across US government sectors since they are mandated by the US government.
Both equips organizations with the best available information for closing infrastructure gaps.
Commvault has validated CIS hardening standards for the core platform infrastructure. Commvault HyperScale storage is pre-hardened using STIGs, so it is ready for deployment across government sectors. In addition to the infrastructure hardening, Commvault digitally signs all binaries included with the Commvault platform to ensure application-level trust.
Air gap and isolation
Data isolation and air gap, the “Air Gap” control concept is a data protection architecture that limits exposure to an attack and allows for data restoration to a point-in-time before the attack began. Commvault can effectively address the risk of encrypted data being replicated in the data backup architecture with; immutable backup targets, periodically applying a WORM security policy to data copies, and removing deletion capability until the retention policy is met. Commvault has improved upon physical access controls available to every solution, enhanced security, simplified, and reduced cost.
Air gap orchestration – automates workflows to orchestrate network and server disconnection.
Network segmentation – uses Network security controls to block incoming access to secondary storage targets both logically and physically.
Encrypted network topologies – use Commvault network policies to isolate communications and create encrypted tunnels outbound from the isolated storage target.
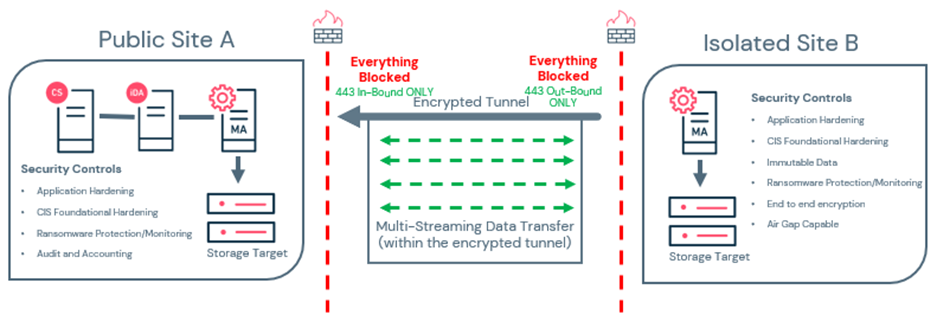
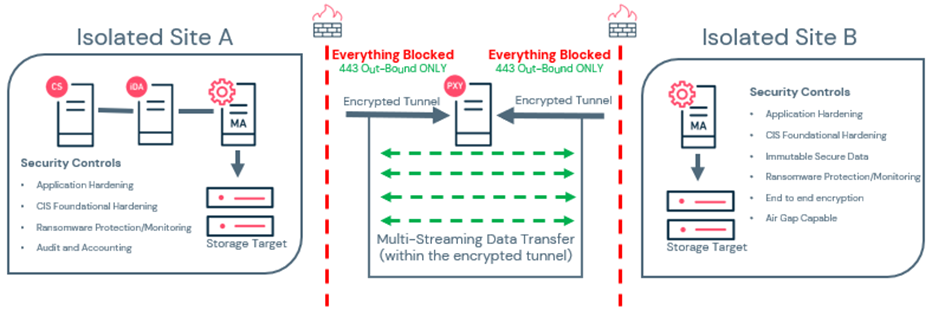
Network topologies, power management, and workflows
Data validation
Ensure that your plan will work as required after implementing the plan in combination with the procedures and technologies which will execute it. Do regular tests to validate that you’re capable of meeting the SLAs defined for critical and high-priority data and applications.
Recovery Orchestration – Commvault main server can be fully recovered with a single click, which can be tested ahead of time by a fully orchestrated test failover to provide a validated restore without disrupting production.
Data Integrity Validation – Commvault provides multiple methods of data integrity validation. Data signatures are used to confirm the integrity of any data transferred, received, and written to storage media. In addition, automated tasks for regularly validating the data on storage are provided.
Backup Validation - a fully orchestrated application recovery validation task can provide access directly to the data protection VM copy from the backup infrastructure, start the application, connect and run a test method, and report back.